- Link to our YouTube channel video: https://youtu.be/58hhRyqNX9s
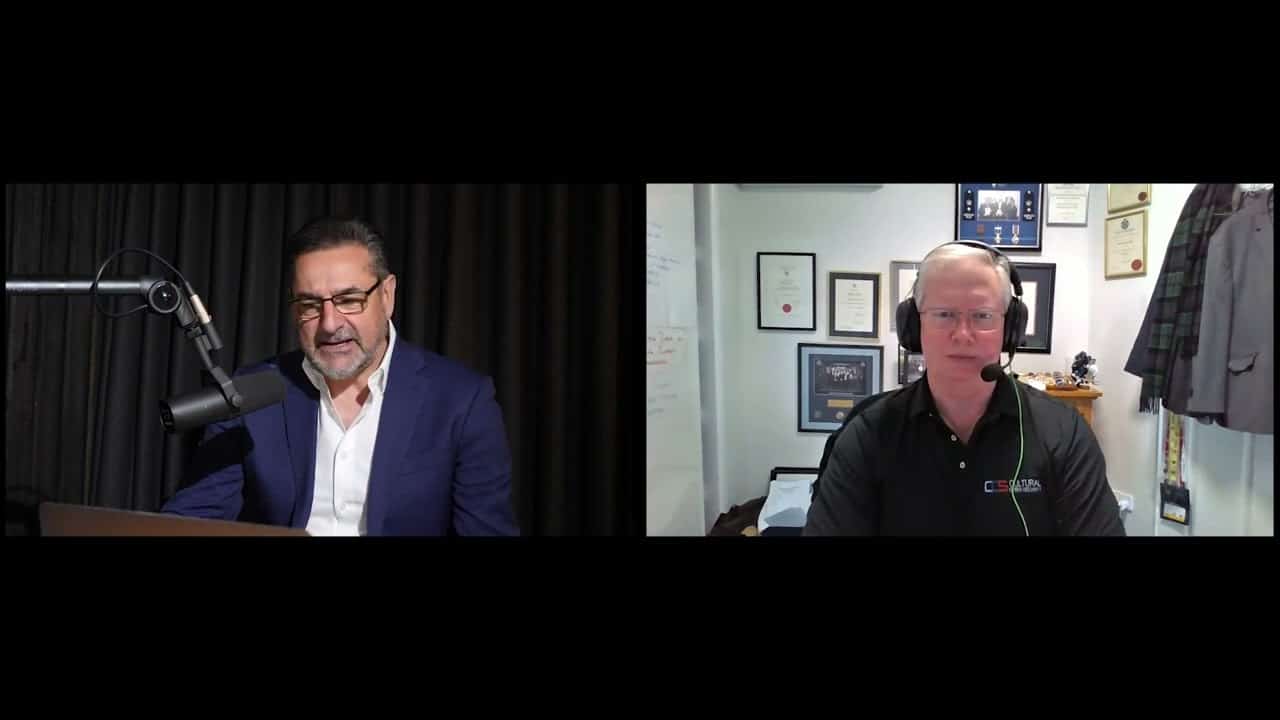
How do you restore Trust after a Cybersecurity attack or breach? Here’s a segment from Brian Hay’s interview with John Dimitropoulos where Brian is drawing analogies between #cybersecurity and the safety and trust of driving a car. Brian argues that both are exercises in risk management that require knowledge, experience, and skills to defend oneself and one’s family. Data breaches are not just incidents but legacies that can have long-term consequences for the victims and that criminals can exploit the data in multiple ways. Security will never be perfect because of human and technological imperfections so we need to accept and manage the risk rather than expect perfection.
At Liberty IT Consulting Group we like to stay close to the most important technology matters. We usually discuss key topics that we believe Execs and Technology industry members will be interested in. This segment’s focus was on #cybersecurity , which should be top of mind for governments, for the private sector and for individuals.
Full Transcript:
John Dimitropoulos:
Data breaches and… unauthorized access to sensitive data, really. We’ve heard one too many stories recently about data breaches. Of course, we heard about Equifax in the US a few years ago, but close to home, of course, Medibank, and most recently Latitude. So beyond the financial and reputational damages suffered by the corporations and also governments, the element that seems to be wounded the most when a breach occurs is trust. How do we restore trust?
Brian Hay:
Yeah, it’s not an easy thing to do. I think we restore trust by building resilience. Accidents occur. You go jump in your car, do you ever stop to think when you get behind the wheel of the car you’re putting your life in your hands? And the answer is no. And do you ever think that driving a car is an exercise in risk management? The more you speed, the greater the risk. The more you increase that risk, the greater the likelihood of a negative consequence. Do you ever stop to think your life is in the hands of other road users? And the answer is no. But we understand there are risks in driving a car. We understand that there’s no guarantee that when next time we drive from point A to point B we won’t have an accident. But what we have done is come to accept it and we’ve come to understand that risk and we’ve come to manage it by wearing seat belts, by having safety devices integrated into the motor vehicle. And the result is today, 3.2 people will still die on Australian roads tragically somewhere today. Hopefully no one here will listen to this, of course. But we accept that risk and we manage it. And what we haven’t done yet is we have this perception of cyber security that it has to be perfect. The truth is it will never be perfect. Why? Because we’ve got humans wearing perfect beings and the technology is never perfect. It’s defeated and reverse engineered as soon as the crooks get their hands on it. So how do we establish trust? I believe we establish trust by giving the public, the people, the knowledge, the experience, and the skills in order to defend themselves and their families. Because we taught our kids from the time they could walk out across the road safely. As our children go up and get their learner’s permits, we teach them, we go through all this process of how to drive a car. But we for babysitting purposes will throw them an iPad and let them use themselves with the vagaries of the internet. So we’ve got a lot of growth to do. So trust is about familiarization with this risk and building the understanding and appreciation of what it means. And it’s going to become more vital, John, because one of the things we tend to view when we have a data breach is we tend to view it as an incident. And quite to the contrary, a data bridge is a legacy. The consequences of that data breach could ensue for decades to come. One of the things we know about the crooks is they understand the value of data. They don’t delete data. It is a commodity that has immense value to them. And so what we will see is the continued aggregation of all this data. Now for example, I’m going to pick a data breach that occurred in Finland about 18 months ago or a bit beyond before that. And it was on a psychology clinic. Then the crooks then came back to the owner’s psychology clinic and said, hey, pay us 400 and I think it was 450,000 Bitcoin or euros and we’ll give you all your data back. And they said, no, go away. We’re not, we’re okay. We don’t need that data back. So then they started going individually to the patients. Now these patients were being treated for mental health issues. They possibly shared the most sensitive secrets that they’ve ever shared with another human in their life. Now crooks are going to say, pay us 200 euros or we’ll expose all your information to the world and we’re going to release the audio recordings of your therapy sessions.
Absolutely horrific. But here’s the thing. If I’m a criminal and I’ve got access to that data, I can make money three ways. One, I can exploit that data myself. Two, I can actually sell that data to other cyber criminals and of course the more I sell it the more profit I make and that’s what I’m in the business of. Or three, I can do a mixture of both. So potentially those poor victims of that could actually be confronted by a new scumbag criminal every month for the next decade trying to extort money based on the sensitivity of that information. So that’s what I mean. It is a legacy. We saw the rise of sextortion emails about two years ago and they’ve started a little bit of a resurgence just recently. What made them so valuable was they could socially engineer the victim to parting with money because they cited their password in the opening sentence of the approach. If you don’t pay this money here’s your password. I’ve compromised your machine. I’m going to do bad things to your reputation. Those passwords came from a LinkedIn data breach I think was 2016 or 2012. So the data always has value. It is a legacy and that’s what we’ve got to understand. So the pathway then to resilience becomes even more vital because this is not something that will go away when it disappears off the front line of the newspaper front page. So trust, it’s an ongoing challenge.
John Dimitropoulos:
Of course, and of course, it becomes more complicated when trust is subcontracted to other entities, for instance, with Latitude, you might have, we, you know, a lot of consumers placed trust into the likes of the Good Guys and David Jones or whatnot, and they got credit through them. But, but that was subcontracted with Latitude, which was behind the scene. So it becomes even more complicated to. You know, to be resilient as well as to safeguard ourselves from such attacks. So thanks for that, Brian.