In an age dominated by the evolution of the smartphone, mankind has never been more connected. Digital 2019 reports from Hootsuite and We Are Social show that 67% of the global population are now connected to the internet via smartphones, with over 5.1 billion unique mobile users. The smartphone is the most adopted tool in human history and many of us use a variety of different applications every day to increase the efficiency or enjoyment of our daily lives. In the process, 2.5 million terabytes worth of new data is created every day. This data has become like gold in the digital age, due to its ability to fuel powerful developments in machine learning, allowing for the production of increasingly effective technology-based products and services.
It is an unfortunate reality these days that for every entrepreneur out there using technology to attempt to better our society, there is an equally as intelligent hacker trying to exploit any vulnerability in data security for profit. This has been especially the case for technology implemented in the financial sector; where the ability to execute digital transactions and the common storage of sensitive information make these applications obvious targets for financially motivated hackers. It seems that every time new security developments are made; hackers find new methods to invade systems and successfully obtain data. This battle for data security has been full of high-profile attacks managing to breach the databases of some of the most well-known financial institutions of our time and this article is going to examine five of them.
5) SONY Pictures Entertainment
SONY is a household name for families all over the world. Their subsidiaries are involved in just about everything from the production of headphones, to large scale motion pictures that are shown in cinemas across the globe. SONY’s various companies employ over a hundred thousand people worldwide, so you can imagine the terror caused when the image below appeared suddenly on SONY company computers one day in 2014, marking the start of a large scale cyberattack against the company.
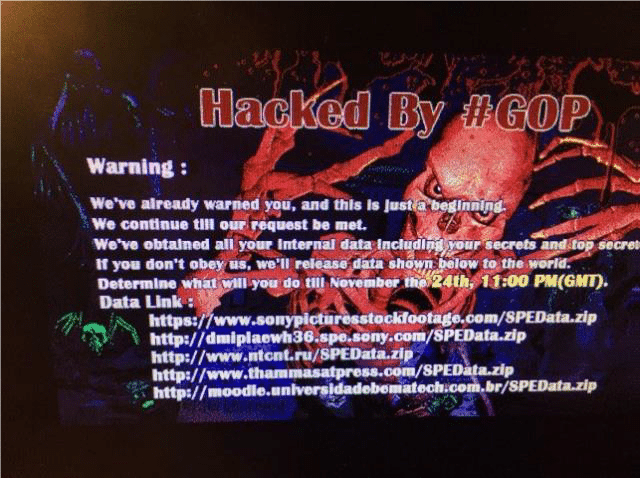
“This image shows the screen that is supposed to have appeared on SONY company computers. The image first appeared on Reddit, posted by someone claiming to be a former employee having received it from a friend still employed at the company.”
The group of hackers, calling themselves GOP (guardians of peace) managed to gain master access to the Sony Pictures Entertainment servers, allowing them to not only access approximately 100TB of company data, but also rewrite and corrupt system files. They later released publicly a huge amount of the data they stole, containing highly sensitive information not only on SONY, but other large-scale corporations and financial institutions. The data leak detailed SONY’s network and security architecture and how to exploit similar systems, as well as huge chucks of raw operations data from interactions with institutions such as Bank of America.
The hackers are believed to have utilised an advanced Server Message Block (SMB) Worm Tool to conduct the attacks and gain access. This highly sophisticated malware contains components that allow it to: “listen” for data, quickly propagate and spread across networks, destroy data past point of recovery, remotely run commands and even rewrite the master boot record of victim machines – rendering them inoperable. Investigations into the attack are ongoing but the US-CERT (United States Computer Emergency Readiness Team) issued a statement linking the malware used in the attack on SONY, to similar malicious hacking tools known to have been utilised by North Korea’s cyberwarfare agency Bureau 121 in previous attacks against South Korea.
4) JPMorgan Chase
JPMorgan Chase is the largest bank in the United States and the world’s most valuable bank by Market Capitalization. The company has trillions of dollars of assets and hundreds of millions of customers across the globe, so you’d be forgiven for thinking that such a company’s sensitive databases of client information were impenetrable. However, in 2014 JPMorgan Chase reported a large-scale cybersecurity breach that resulted in 76 million account holders having highly sensitive financial information stolen.
Hackers accessed a web server portal that allowed certain employees access for web development. This level of server access could be obtained through only a username and password combination – without any two factor authentication requirements that have become standard practice throughout the cybersecurity industry. This made it easy for the hackers to gain access to this server initially and dig around for further information to gain higher levels of access. Progressing this way, the attackers ended up gaining access to over 90 Servers containing highly sensitive client information and communications between these clients and staff members. No funds have ever been reported stolen as a result of the hack, however the breach of the largest financial institution in the U.S. was seriously alarming for global finance in an increasingly digital age.
3) Equifax
Equifax is one of the world’s largest consumer credit reporting agencies, collecting and aggregating sensitive information from over 800 million individual consumers and more than 88 million businesses. In 2017, Equifax announced a data breach where attackers accessed Equifax consumers’ personal data, containing full names, birthdates, addresses and social security numbers.
The hackers exploited a vulnerability in the application servers of the Equifax Automated Consumer Interview System (ACIS), that was known to homeland security. Equifax was given direct warning from homeland security to patch effected servers, however due to faults in their vulnerability scanners, the system weaknesses were not identified or patched. After gaining access through the application server, hackers were able to access over 45 different databases containing approximately 143 million records of highly sensitive customer information. The information was then slowly exported through the same server vulnerability, occurring undetected due to yet another bug in the Equifax ACIS architecture. This time, outdated certificates on the SSL Visibility Appliance meant that it wasn’t inspecting all of the traffic to and from the servers. The IT team updated the certificates at the same time the attack was still occurring and were able to confirm that sensitive data was being exfiltrated to 35 different IP addresses in China.
While this attack did not result in any stolen funds, it was a shocking revelation for consumers all across the globe and highlighted the daunting fact that cybersecurity vulnerabilities exist even at the highest level of data sensitivity. This is a case where personal information was a clear target in the attack and indicates either a mass surveillance attempt or a financially motivated hacker stealing this information with the intension of selling it on the black-market.
2) SWIFT / Bangladesh Central Bank
The Society for Worldwide Interbank Financial Telecommunication (SWIFT), provides a network that allows financial institutions from all across the globe to send and receive highly sensitive transaction information in a secure manner. This network is the largest of its kind, and as of 2018 approximately half of all cross-border payments were facilitated by SWIFT.
Although the network does not directly provide fund transfer services; in February 2016 hackers managed to exploit SWIFT to create fraudulent bank orders from the Bangladesh Central Bank (BCB), successfully transferring over $100 million USD to bank accounts in Sri Lanka and the Philippines. Through penetrating the data systems of member banks, the attackers were able to obtain legitimate SWIFT credentials and create the fraudulent orders undetected. Interestingly the hackers could have made off with a further $850 million, however a repeat spelling error in many of the fraudulent transactions led to them being flagged and blocked by the Reserve Bank of New York.
Investigation was conducted by two independent US security firms, both reporting that the SWIFT attack was likely orchestrated by the same group of hackers that were behind the 2014 hack on Sony Entertainment, due to similarities in the malware used to obtain restricted access. The group has been nicknamed “Lazarus Group” by researchers and are believed to be linked to North Korea. If the connection to this group and North Korea is true, the attack on the SWIFT network is the first known occurrence of a state using cyberattacks to effectively rob a bank.
1) Mt. Gox. Exchange
Mt. Gox. was a cryptocurrency exchange based in Japan that launched in 2010. By 2014, it was the world’s largest cryptocurrency exchange, handling over 70% of bitcoin transactions at the time. In February of 2014, Mt. Gox. suspended trading and filed for bankruptcy protection. They later announced that approximately 850,000 bitcoin (worth more than $450m USD at the time) belonging to customers was missing and likely stolen. Suspiciously, 200,000 of this bitcoin has since been “found”, raising questions about the legitimacy of the exchange and more directly it’s CEO of the time, Mark Karpelès.
It was determined that the BTC was stolen directly from the Mt. Gox. hot wallet* gradually over time, with the attack starting as early as 2011 – *A hot wallet is a term used to describe a cryptocurrency wallet that an exchange such as Mt. Gox. uses to house large pools of its users’ assets to allow for the rapid distribution required to operate an exchange. Karpelès was arrested by Japanese police in August 2015 and charged with fraud and embezzlement. He was accused of misappropriating ~2.6m USD worth of user funds into an account under his own control, approximately six months before the exchange collapsed. Karpelès was later acquitted of these charges but found guilty of falsifying data, with the court stating that “the charge of electronic record tampering is true and deserves punishment, but there’s no criminal evidence of embezzlement”.
Author: Hailey Romeo – Liberty IT Head of Marketing